Microsoft is currently leveraging the MITRE ATT&CK framework within Microsoft Sentinel. This capability is provided to help you view threats already detected and to help you understand how your environment maps to the tactics and techniques of the MITRE ATT&CK framework. Whereas these activities are primarily aligned to the Operational Security Assurance side of the house, threat modeling is part of the Security Development Lifecycle practices of Secure DevOps. This article will describe how to create a template that aligns to the tactics and techniques of the MITRE ATT&CK framework. In the past I have created threat models that lean on the techniques of the ATT&CK framework, but were aligned to the STRIDE model. This template will be aligned to the MITRE ATT&CK framework.
I will work forward, making decisions and testing the expected results, and go back and adjust as needed. The primary goal is that during the SDL process, to leverage the Microsoft Threat Modeling tool to drive design and engineering decisions, and to test these results with the simulation outputs from Microsoft Sentinel.
The first step is to create a model that represents how the ATT&CK framework will be aligned to the features of the Microsoft Threat Modeling tool.
I will work forward, making decisions and testing the expected results, and go back and adjust as needed. The primary goal is that during the SDL process, to leverage the Microsoft Threat Modeling tool to drive design and engineering decisions, and to test these results with the simulation outputs from Microsoft Sentinel.
The first step is to create a model that represents how the ATT&CK framework will be aligned to the features of the Microsoft Threat Modeling tool.
The ATT&CK Object Model has the following relationships:
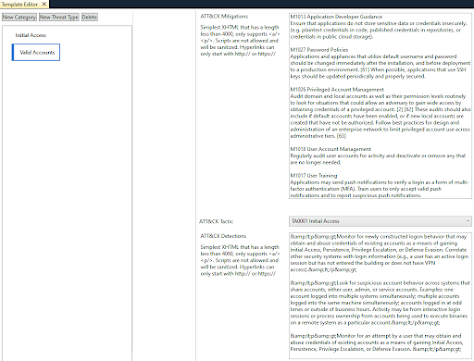
For our template, we will use the Threat Model Category to align to MITRE ATT&CK Tactic and we will align the Threat Type to the MITRE ATT&CK Technique.
We will define the data sources as stencils and derive stencils will be the actual implementation of the data source. For example, the data source Cloud Storage will be the Stencil and Azure Storage will be the derived stencil as shown below.
This gives us a good foundation for laying out the MITRE Tactics and Techniques.
The template and samples will be provided on Github @ Security-Threat-Models
In the next part of this blog series, we will outline the initial scenarios and provide the samples and outcomes. Stay Tuned!





No comments:
Post a Comment